This page would list out the major differences between RHEL 8 and 7 variants and key features in RHEL 8. Red Hat has changed the…
OS
okd – The Origin Community Distribution of Kubernetes that powers Red Hat OpenShift.
Built around a core of OCI container packaging and Kubernetes container cluster management, OKD is also augmented by application lifecycle management functionality and DevOps tooling….
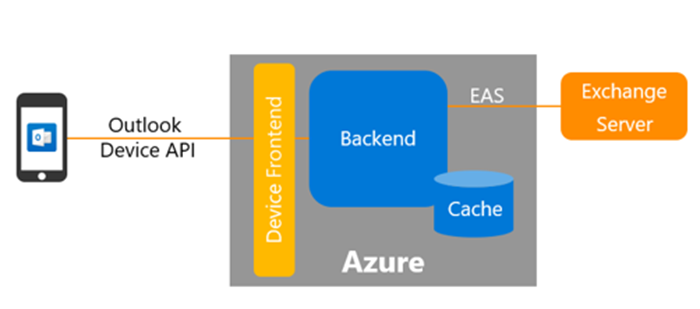
Be careful: Microsoft Outlook iOS app is using Azure cloud services to process, store and cache your email data
I tried out the Microsoft Outlook app on iOS. Checking what kind of features this product might bring to me or my customers. Since I…
Changes between Red Hat Enterprise Linux 6 and 7
The distribution RHEL 7.x comes with a lot of changes on the administration side. Make sure you are aware of those and plan the migration…
34C3 – Chaos Computer Congress
This year, the Chaos Computer Congress opened his doors in Leipzig. About 15000 visitors joined the presentation & questions sessions. All sessions have been recorded…
R.E.A.R. – Relax and Recover
Relax-and-Recover has a few interesting characteristics you may find useful when assessing it as a Disaster Recovery solution: Modular design, written in Bash easy to…